A couple of weeks ago, the MacStories team shared our favorite indoor HomeKit devices. The HomeKit accessory universe is more limited outdoors, but with spring easing into summer in the Northern Hemisphere, we thought we’d share the devices that we use outside, too.
Looking Past the Smoke and Mirrors of the MGM Hack [Sponsor]
The September 2023 MGM hack quickly became one of the most notorious ransomware attacks in recent memory. Journalists and cybersecurity experts rushed to report on the broken slot machines, angry hotel guests, and the fateful phishing call to MGM’s help desk that started it all.
And, like a slick magic trick, the public’s attention was drawn in the wrong direction. Now, months later, we’re still missing something critical about the MGM hack.
That’s because, for many of the most important questions about the breach, the popular answers are either incomplete or inaccurate. Those include: who hacked MGM, what tactics they used to breach the system, and how security teams can protect themselves against similar attacks.
Why is that a problem? Because it lets us write off the MGM hack as a one-off story, instead of an example of an emerging style of attack that we’ll certainly be seeing more of. And that leaves companies and security teams unprepared.
Who hacked MGM?
Plenty of news stories have confidently blamed the MGM attack on either the Scattered Spider or ALPHV hacking group, but the truth is still murky, and likely involves a dangerous team up between different groups, each bringing their own expertise to the table.
Their attacks first use fluent English social engineering skills to get onto networks, where they then deploy sophisticated ransomware that quickly establishes persistence across multiple systems.
What tactics did they use?
The dominant narrative has been that “a single phone call hacked MGM.” A phone vishing attack to MGM’s IT help desk is what started the hack, but there’s much more to it than that. The real issue is that this help desk worker was set up to fail by MGM’s weak ID verification protocols, and probably wasn’t doing anything “wrong” when they gave the bad actors access to a super administrator account.
How can security teams protect themselves?
Cybersecurity experts have centered most of their advice on user ID verification. But while it’s true that MGM’s help desk needed better ways of verifying employee identity, there’s another factor that should have stopped the hackers in their tracks.
That’s where you need to focus your attention. In fact, if you just focus your vision, you’ll find you’re already staring at the security story the pros have been missing.
It’s the device you’re reading this on.
To read more of what we learned when we researched the MGM hack–like how hacker groups get their names, the worrying gaps in MGM’s security, and why device trust is the real core of the story–check out the Kolide Blog.
Our thanks to Kolide for sponsoring MacStories this week.
Listen Later: Listen to the Articles as Podcasts [Sponsor]
Listen Later gets you through that huge pile of web articles you’ve been saving for later. Let’s face it, the web is a big place, and there’s always more to read than you have time for. Read-later apps give you a place to save articles for later, but you still need to find the time to read everything you saved.
Listen Later helps you get through that stack of articles by combining the power of podcasts and AI. Simply send Listen Later a link to an article and its AI converts the text into a narration using one of its natural-sounding AI voices. Each article becomes an episode of your very own personal Listen Later podcast. Listen Later works with text from images, PDFs, and other text documents and can translate articles to other languages, too.
It’s easy to add your Listen Later podcast to your favorite podcast player, making it available whether you’re driving to work, out for a long walk, or simply hanging out. Best of all, though, by converting your articles to audio, Listen Later greatly expands the time you can spend on your read-later queue.
What’s more, with Listen Later, you never spend more than you need. You buy credits, which are used as you add articles to your podcast feed. When you’ve used up your credits, you can reload them automatically or purchase more manually. How much you spend is completely up to you.
Visit Listen Later today to learn more, sign up for free, and receive $2 in free credits to convert articles to audio.
Our thanks to Listen Later for sponsoring MacStories this week.
HomeKit Gadgets: The MacStories Team Collection
John: Everyone on the MacStories team is deep into HomeKit devices. For me, smart home gadgets tick all the boxes:
- Hardware
- Software
- Automation
It’s really as simple as that.
However, as fun as HomeKit devices can be, they can also be frustrating. The best accessories fit comfortably into your household, making life a little easier but falling back gracefully to a simple solution for anyone in your home who isn’t interested in automation. It sounds easy, but it’s a tough balancing act that few companies get right.
We’ve all tried our share of HomeKit and other smart home devices. Some have worked out, and others have fallen by the wayside as failed experiments. Today, we thought we’d pool our collective experience and share with you the MacStories team’s favorite smart home gadgets.
We have a lot of ground to cover, so this story will focus on indoor gadgets. Soon, we’ll shift our focus to the great outdoors.
[table_of_contents]
Are You Worse at Security Than the TSA? [Sponsor]
You know the drill: when you go through airport security there are two lines. In one, a TSA agent makes sure you’re the person in your passport photo. In the other, a machine scans your carry-on for explosives, weapons, or a normal-sized bottle of shampoo.
Enterprise security is much the same, but instead of passengers and luggage, we’re talking about end users and their devices. In the first line, user authentication verifies a user’s identity, and it’s gotten pretty sophisticated in the past few years, with SSO and MFA becoming more common.
But user devices don’t get nearly the same level of attention. The average device trust solution only looks at a handful of endpoint security factors, like OS updates and firewall. If this really were the TSA, that wouldn’t even be an x-ray machine, more like holding a bag to your ear and listening for a ticking sound.
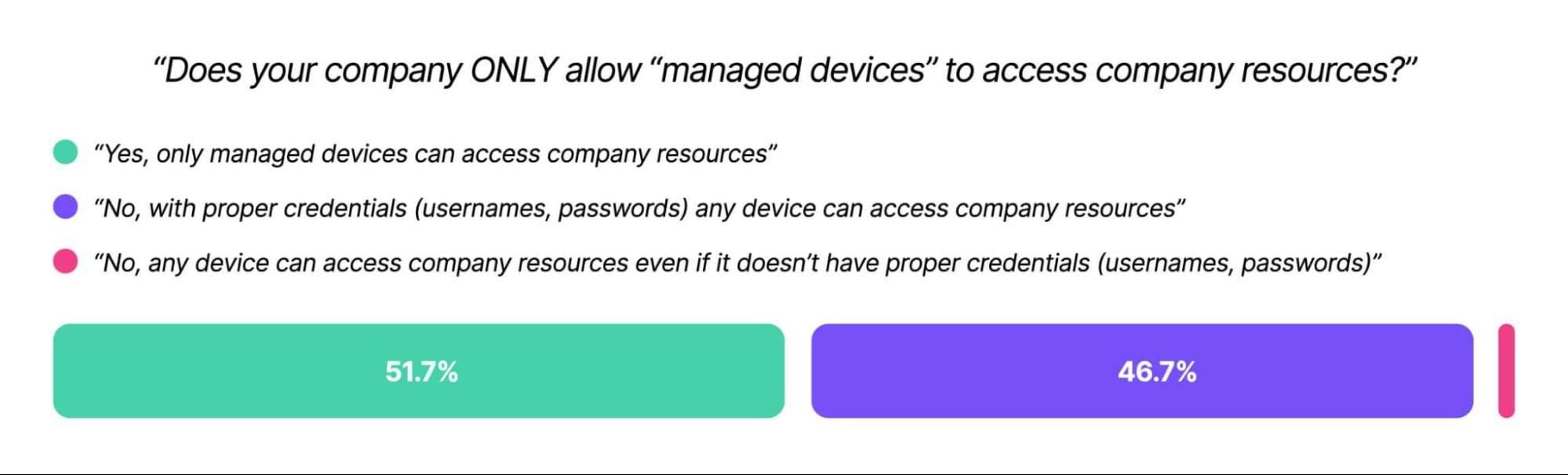
And that’s assuming an organization looks at end user devices at all. Kolide’s Shadow IT report found that 47% of companies let unmanaged devices access their resources, and authenticate via credentials alone.
Unmanaged devices (those outside a company’s MDM) can be infected with malware, full of PII, or worse–they can belong to a bad actor using phished employee credentials.
And hey, there are valid reasons for a device not to be enrolled in MDM. Contractor devices, Linux machines, and employee phones all need to be able to access company resources. But there’s plenty of room for middle ground between “fully locked down and managed” and an open-door device policy.
Specifically, companies need device trust solutions that block devices from authenticating if they don’t meet minimum security requirements.
Even with phishing-resistant MFA, it’s frighteningly easy for bad actors to impersonate end users–in the case of the MGM hack, all it took was a call to the help desk. What could have prevented that attack (and so many others) was an unspoofable form of authentication for the device itself.
That’s what you get with Kolide’s device trust solution: a chance to verify that a device is both known and secure before it authenticates. Kolide’s agent looks at hundreds of device properties (remember, our competitors only look at a handful). What’s more, our user-first, privacy-respecting approach means you can put it on machines outside MDM: contractor devices, mobile phones, and even Linux machines.
Without a device trust solution, all the security in the world is just security theater. But Kolide can help close the gaps. (And we won’t even make you take off your shoes.)
To learn more, please watch our on-demand demo.
Our thanks to Kolide for sponsoring MacStories this week.
Struggling to Afford Cybersecurity Insurance? Here’s Why. [Sponsor]
When MGM Resorts suffered a $100 million hack in September, CEO Bill Hornbuckle wasn’t too worried about the lost revenue, because cyber insurance would cover the tab. “I can only imagine what next year’s bill will be,” he joked.
Weeks later, on a call with analysts, Hornbuckle complained about the “staggering” rise of insurance costs in the past few years.
This story neatly illustrates the crisis in cyber liability coverage. For years, companies have invested more in security insurance than in actual security. The result has been a tidal wave of data breaches that have driven up the cost of premiums to the point that they are rapidly becoming unaffordable.
Some large enterprises are responding to the increased costs by creating their own “captive carriers,” insurance providers that exist only to serve them. But that’s clearly not an option for small businesses, which are more likely to go without insurance altogether.
According to Andrew Bucci, VP of Sales at Amplified Insurance Partners, “It’s going to come to a point where some people may have to self-insure, which means that they don’t take a cyber policy out and they just cross their fingers they don’t have some sort of breach.” That’s a huge gamble for SMBs, since they could be driven to bankruptcy by a single security incident.
At Kolide, we’ve seen our cyber insurance premiums go up by 40% in just the last two years, and we got curious about:
- What’s driving the increases?
- Who really needs cybersecurity insurance?
- How can the average company reduce their premiums?
What we found was that insurance companies themselves can help get us out of this crisis, by mandating some (pretty basic) security requirements for their customers–things like MFA, endpoint security, and retiring end-of-life software.
Read the full blog to learn more about our findings.
Our thanks to Kolide for sponsoring MacStories this week.
FastMinder: A Simple, Lightweight, and Clutter-Free Intermittent Fasting Tracking Experience [Sponsor]
Funn Media knows that the best tracking apps make it easy to get started and even simpler to stick with your tracking. That’s exactly what FastMinder, its new iPhone, iPad, and Apple Watch app for tracking intermittent fasting, does.
Funn Media’s years of experience developing apps like WaterMinder and Calory show in FastMinder. The app is beautifully designed, making it easy to set up a fasting window with popular presets or a completely custom schedule.
Once you set up your fast and begin, you can track your progress using FastMinder’s Home Screen widgets and Live Activity. Then, over time, you can chart your progress with FastMinder’s Stats tab, tracking the number of your fasts and their length, your current streak, weekly, monthly, and yearly totals, and more. FastMinder also incorporates weight, hydration, and setup tracking, providing the sort of context that many other apps don’t.
FastMinder also includes custom reminders to help keep you on track and insights into the benefits of each stage of a fast. And, with version 1.2, FastMinder will soon add Solar Fasting to its feature set.
If you’ve decided to explore the health benefits of intermittent fasting, make it easier to get started and stay on track by downloading FastMinder from the App Store today.
Our thanks to Funn Media and FastMinder for MacStories this week.
Voice Clones Have Crossed the Uncanny Valley [Sponsor]
Now, don’t get offended, but – you aren’t as good at clocking deepfakes as you think you are.
And it’s not just you–nobody’s that good at it. Not your mom, or your boss, or anyone in your IT department.
To make matters worse, you probably think you can spot a fake. After all, you see weird AI-generated videos of celebrities on social media and they give you that uncanny valley tingle. But it’s a different ballgame when all you’ve got to go on is a voice.
In real life, people only catch voice clones about 50% of the time. You might as well flip a coin.
And that makes us extremely vulnerable to attacks.
In the “classic” voice clone scam, the caller is after an immediate payout (“Hi it’s me, your boss. Wire a bunch of company money to this account ASAP”). Then there are the more complex social engineering attacks, where a phone call is just the entryway to break into a company’s systems and steal data or plant malware (that’s what happened in the MGM attack, albeit without the use of AI).
As more and more hackers use voice cloning in social engineering attacks, deepfakes are becoming such a hot-button issue that it’s hard to tell the fear-mongering (for instance, it definitely takes more than three seconds of audio to clone a voice) from the actual risk.
To disentangle the true risks from the exaggerations, we need to answer some basic questions:
- How hard is it to deepfake someone’s voice?
- How do hackers use voice clones to attack companies?
- And how do we guard ourselves against this… attack of the clones?
Like a lot of modern technologies, deepfake attacks actually exploit some deep-seated fears. Fears like, “your boss is mad at you.” These anxieties have been used by social engineers since the dawn of the scam, and voice clones add a shiny new boost to their tactics.
But the good news is that we can be trained to look past those fears and recognize a suspicious phone call–even if the voice sounds just like someone we trust.
If you want to learn more about our findings, read our piece on the Kolide blog. It’s a frank and thorough exploration of what we should be worried about when it comes to audio deepfakes.**
Our thanks to Kolide for sponsoring MacStories this week.
Whisper Memos: Turn Your Ramblings into Paragraphed Articles, Sent Right to Your Email Inbox [Sponsor]
Ideas are precious but fleeting. One moment, inspiration strikes, but if you don’t capture that lightning in a bottle, it’s gone before you know it. With Whisper Memos, you can harness the power of artificial intelligence to turn your ideas into orderly memos.
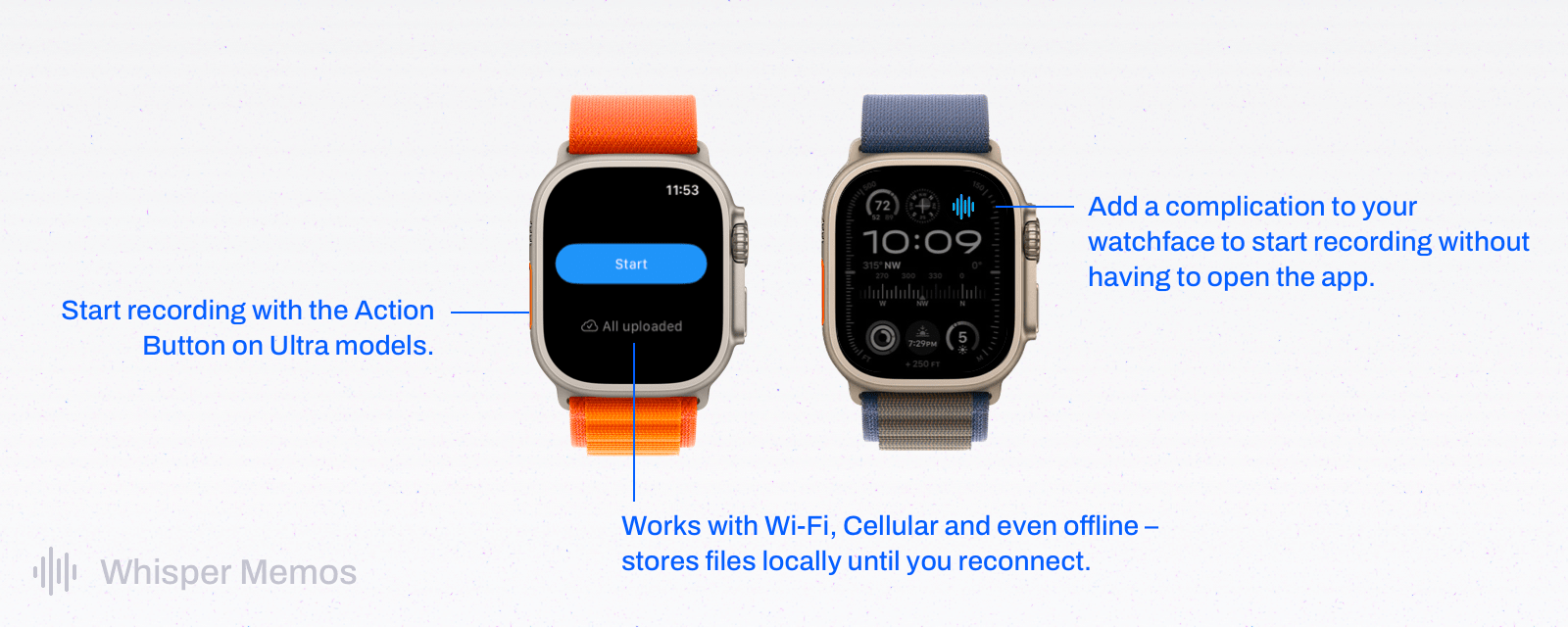
Whisper Memos combines the convenience of quick capture with the power of GPT-4. You can save a voice memo using your iPhone’s Action Button, the app’s Lock Screen widget, Whisper Memos’ Apple Watch app, Shortcuts, and more. Then, Whisper Memos uses AI to turn your recordings into orderly, paragraphed memos delivered directly to your email inbox a few seconds later.
The results are incredible. One moment, you’re recording audio on your iPhone or Apple Watch, and the next, you’ve got an email message easily identifiable by its custom subject line that has been carefully transcribed and organized into neat paragraphs.
Whisper Memos works on Wi-Fi, over a cellular connection, and offline, so it’s always available. The app also supports a long list of languages, and it integrates with Zapier, which allows you to connect Whisper Memos to other productivity apps like Notion, Trello, or your task manager. There’s even a privacy mode for ensuring no trace is left behind after your voice memos have been processed.
So, check out Whisper Memos today and use the code MAC24 by March 16th for 25% off forever. You’ll be amazed at how fast, accurate, and reliable it is at preserving your precious thoughts.
Our thanks to Whisper Memos for sponsoring MacStories this week.